The Essential Guide to Implementing STIR/SHAKEN
Updated on January 18, 2024
At the time of writing this guide, we’re already a year past the point when the FCC made it mandatory to implement STIR/SHAKEN for all carriers operating in the US.
Most of the big carriers have already implemented STIR/SHAKEN. However, there remains a sizable proportion of carriers who’re yet to come on board.
This article is meant for these carriers and anyone looking to become a service provider in the coming future.
This article will guide you through all the steps necessary for implementing STIR/SHAKEN so your calls are not blocked or labeled as scam calls.
So let’s get started, shall we?
Prerequisites for Implementing STIR/SHAKEN
Before you can implement the STIR/SHAKEN protocol, you need to complete a few steps in the process and acquire certain tokens and certifications.
Let’s get to know about all the prerequisites!
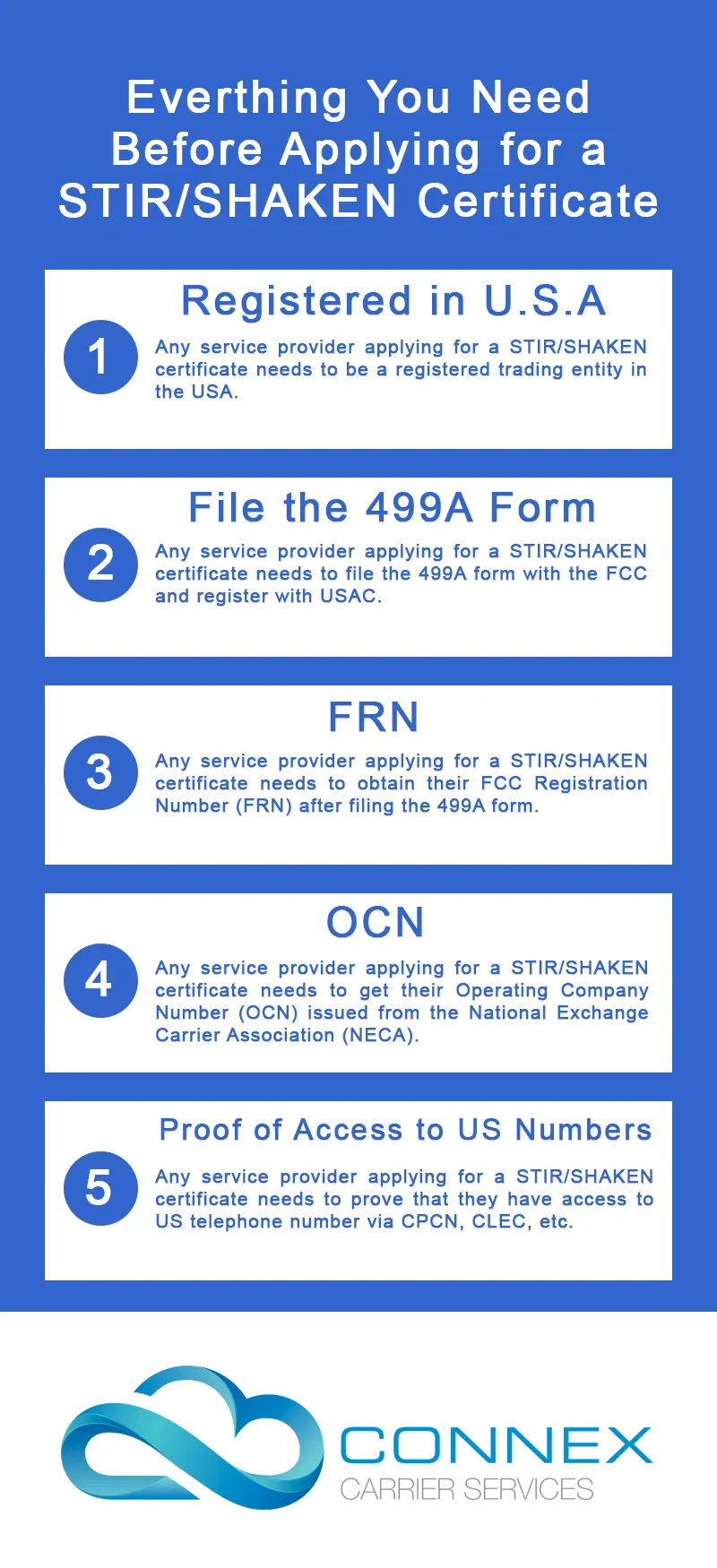
You must be a Trading Entity registered in the US
STIR/SHAKEN protocol is an initiative brought up by US’s FCC to curb ID spoofing and malicious robocalls. The primary prerequisite for implementing the STIR/SHAKEN protocol is that you need to be a trading entity registered in the US.
File the 499A form with the FCC
All service providers have to fill out the FCC form 499A and register with the Universal Services Administrative Company.
Filers are required to report the company’s actual revenue billed during the previous calendar year.
Get FCC Registration Number (FRN)
After filing the FCC form 499A, you will be issued a FCC Registration Number (FRN). An FRN is essential as it links your TIN (Taxpayer Identification Number) to FCC registration.
All companies and individuals are required to provide their TIN to do business with any federal agency.
To get an FRN, you will have to register yourself with the FCC Commission Registration System (CORES). Once you are registered, you will be provided with an FRN and a password that is linked to your TIN.
Here is the information you will need to provide for the registration.
- Taxpayer Identification Number (TIN). For individuals, this is a Social Security Number and for businesses, this is an Employer Identification Number
- The name of the individual or business
- Type of business
- Contact information
- Password
- Personal Security Question (PSQ) and answer: Your PSQ and answer are not case sensitive.
Operating Company Number (OCN)
Operating Company Number, also known as Company Codes are unique identifiers assigned to every telecommunications service provider by the National Exchange Carrier Association (NECA).
OCNs are also used in mechanized and legacy systems to enable the transmission of information throughout the network.
Here are the steps you need to follow to get an OCN.
- Fill in and submit the Incumbent Company Code Request form.
- Fill in and submit the Company Code Request form. The instructions can be found here.
For Non-ILEC codes (CLEC, ULEC, CAP, IC, IPES, ETHX, LRSL, WIRE, WRSL, PCS, and PCSR) – The following information is required to obtain a Company Code.
- Company Code request form
- Legal documentation (e.g. Articles of Incorporation with state seal or stamp, State Registration, etc.) as proof of existence and to reflect the service provider’s legal name;
And for:
*CLEC, ULEC, CAP, LRSL codes – a copy of the certification by the state public utilities commission;
IC codes - Documents may vary from state-to-state. A copy of the state public utilities commission approval is required when the state commission regulates the interexchange carrier/reseller service. If the service is not regulated by the state commission, the required documentation may vary. Therefore, please contact the 09-2023 Company Code Administrator at [email protected] or 973-884-8105.
IPES codes - proof of service and proof of customers, e.g., interconnection agreements (or evidence of an interconnection order pursuant to an approved tariff) and contractual agreements or an invoice with end-user customers showing proof of customer, or regulatory administration approval, if applicable. Additionally, a detailed description of the type of service being provided including the areas where the service will be provided. We reserve the right to request additional documentation.
ETHX codes - proof of service and customers, e.g., contractual agreements with customers and a detailed description of the service including the areas where the service will be provided. NECA reserves the right to request additional documentation.
Wireless or PCS codes - a copy of the company’s FCC radio/PCS license;
Wireless and PCS Resellers - a copy of the interconnection agreement with the wireless carrier.
OCN Registration Fee Structure
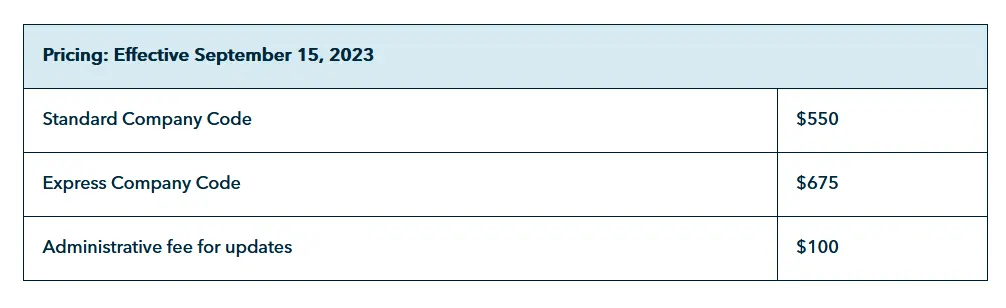
You will have to register with NECA and get your OCN prior to moving ahead with the implementation of STIR/SHAKEN. For detailed instructions, please refer to this document. Or if you want a detailed explanation on how to acquire your OCN, please refer to our blog here.
Proof of Access to US Telephone Numbers
You are also required to prove that you have access to US telephone numbers.
You can do this via producing a Certificate of Public Convenience and Necessity (CPCN), Competitive Local Exchange Carrier (CLEC) certificate or proof of direct access to US numbers.
Once you have all of the above-mentioned information, you can proceed with getting the STIR/SHAKEN token and then the certificate.
4 Easy Steps to Procure STIR/SHAKEN token and certificate
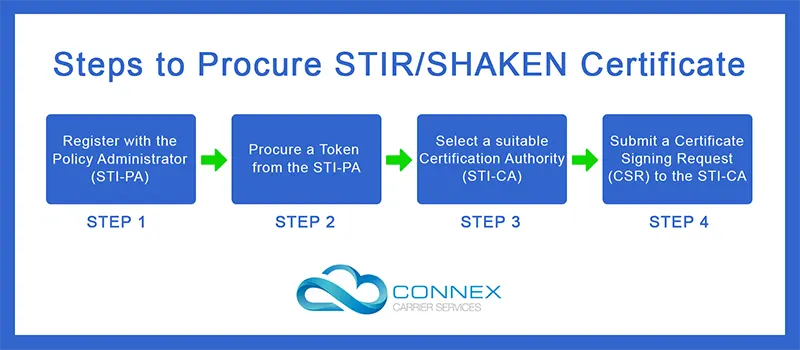
Register with the Policy Administrator
A policy administrator evaluates and authorizes certain trusted third parties to act as Certification Authorities and issue STIR/SHAKEN certificates to service providers.
Iconectiv is the policy administrator in the US and is responsible for coordinating, registering and verifying certification authorities based on the tight guidelines issued by the Secure Telephone Identity Governance Authority (STI-GA).
Once the service provider is registered with the Policy Administrator, they can proceed to the next step in the process.
Procure a token from Policy Administrator
A carrier or service provider is expected to request a service provider code or token from the Policy Administrator.
The Policy Administrator will ask for all the necessary information it requires from the carrier or service provider in order to validate them.
Once validated, the Public Administrator will provide the carrier or service provider with a token that contains the carrier’s unique identifier (SPID) and OCN.
Once the process completes and the token is procured, the carrier and service providers can proceed to the next step.
Selecting a Certification Authority
Secure Telephone Identity Certification Authorities (STI-CAs) are a vital component of the STIR/SHAKEN framework.
These Certification Authorities are responsible for assigning digital certificates to carriers and service providers which are used to authenticate their Caller ID.
Only the certification authorities approved by the STI-PA are allowed to issue STIR/SHAKEN certificates to carriers and service providers.
The call authentication process involves the terminating carrier service checking the originating service provider’s certificate is issued by a proper STI-PA approved Certification Authority.
ConnexCS recommends its users use Sansay as their STI-PA-approved certification authority, however we will be compatible with certificates issued by all CA’s.
Requesting a Certificate
In order to be issued with a STIR/SHAKEN certificate, a carrier or service provider is required to submit a Certificate Signing Request (CSR).
They are supposed to send in their CSR along with their token to the certification authority. Once the application is approved, the Certification Authority issues a STIR/SHAKEN certificate to the carrier or service provider.
A Certification Authority checks for the following before approving the CSR:
- Validating Service Provider Code (SPC) token issued by the STI-PA.
- Accepting Certificate Signing Requests (CSRs) for SHAKEN certificates.
- Issuing standards-compliant SHAKEN signing certificates, including the Telephone Number Authorization List (TNAuthList) extension.
- Publishing certificates to a hosted STI-Certificate Repository (STI-CR) for relying parties.
- Revoking certificates if needed and notifying the STI-PA.
- Accepting Certificate Signing Requests to renew them before they expire.
- Sharing the Neustar root STI-CA public certificate to support SHAKEN call verification and chain validation.
With that, you have all that is needed to start implementing the STIR/SHAKEN protocol.
How to Implement STIR/SHAKEN with ConnexCS?

A STIR/SHAKEN certificate is a necessity for origination service providers to authenticate all outgoing calls. With the implementation of the STIR/SHAKEN protocol, the FCC plans to minimize the evils of ID spoofing and scam calls.
In order to implement the STIR/SHAKEN protocol with ConnexCS, all you have to do is add your certificate to your account.

Once you have added the certificate, ConnexCS will begin signing all outbound calls with your certificate.
























































































































