VoIP Carrier's Ultimate Guide to Cleaning Up Their Traffic
As VoIP Carriers, I'm sure most of you have first-hand experience with how the general state of things are in the industry. Spam and scam calls are growing at an alarming rate. A 118% rise in spam and scam calls was reported in 2021 compared to 2020.
The majority of VoIP carriers have knowingly or unknowingly played a part in this rise in spam and scam calls. Now don’t get me wrong, I know VoIP carriers aren’t directly responsible for this. However, enabling fraud even unknowingly is still wrong.
Every victim of a spam or scam call has on average, lost $567 to these frauds. The numbers are staggering and all VoIP carriers should be concerned about this.
VoIP carriers stand to lose a lot of business if the general population develops a mistrust for VoIP technology as a whole.
Thus, everyone in the VoIP industry needs to take corrective actions to ensure these spam and scam calls are minimised. There are multiple ways to do so and we shall cover this in our blog.
Before we get to that section, let’s cover some basics to begin with!
A Brief Overview of the Growing Menace of Spam and Scam Calls in the VoIP Industry

The TL;DR is that technological advancements have made scamming more effective using VoIP technology. The rise in scam and spam calls can directly be attributed to how easy it is to set up VoIP systems and manipulate Caller IDs.
So it shouldn’t surprise you to know that 31.1 billion scam calls were reported just in the first 3 quarters of 2022. While this number is quite astonishing in itself, the number of people who fell victim to such scams increased by up to 270%.
It shouldn’t surprise you that almost a quarter of all global spam and scam calls were aimed at residents in the United States. How much did US citizens lose to such scams? A staggering $29.8 Billion!
The rise in the effectiveness of such scams can be attributed to caller ID and neighbourhood spoofing. Technology has made it easy for scammers to make their calling numbers look like ones from your neighbourhood or from a legitimate government authority.
While governments around the world are trying to curb this menace, their efforts are falling short. The FCC has implemented STIR/SHAKEN to combat Caller ID spoofing. However, the system hasn’t seen wide-scale success in eliminating scam calls.
I know what you’re wondering, why should you care about all of this? There are a few important reasons why, let me highlight those for you!
Why Should VoIP Carriers Be Concerned About The Rise In Spam and Scam Calls
1. Hefty Fines

The FCC and FTC can impose fines on VoIP carriers for carrying spam and scam call traffic. The specific fines vary depending on the circumstances of the violation and the severity of the offence.
The FCC has the authority to impose fines for violations related to unlawful robocalls and spoofed caller ID information.
The FCC can levy fines of up to $10,000 per violation. In cases where the violation is deemed intentional or willful, the fine can increase significantly, reaching up to $16,000 per violation.
Please note that the fine amounts are per single violation. Any medium-sized VoIP carrier carries anywhere around 500,000 to a million calls in a single day.
Even if 0.1% of your daily traffic is scam or spam calls, it would result in an astronomical amount of fines being imposed upon you!
2. Increased Regulatory Compliances

Increasing regulatory compliance requirements due to spam and scam calls can have several negative impacts on the business of a VoIP carrier.
To start with, compliance with regulatory requirements often entails more complex operational processes. This would include filtering and monitoring calls more strictly and employing compliance officers to keep everything in check.
VoIP carriers may need to dedicate more resources to ensure compliance. This may include deploying additional resources for monitoring and filtering calls in the form of servers and manpower in the form of compliance officers.
This increased operational burden can lead to additional administrative work. VoIP carriers will not only have to maintain this additional infrastructure but also manage the additional human resources.
So a VoIP Carrier will in turn have less time to dedicate to growing the business.
3. Legal and Regulatory Concerns

If you’re not careful with what type of traffic you carry, you may end up in trouble on multiple fronts. I hope you already have an idea about how things can take a turn for the worst when it comes to being prosecuted in the USA and being found guilty.
The FCC actively takes action against VoIP carriers that facilitate spam and scam calls. The FCC can impose fines, penalties, and other enforcement actions for violations.
These violations include regulations related to robocalls, call spoofing, call authentication, and consumer protection. These enforcement actions can have legal and financial consequences for the carrier.
The Federal Trade Commission (FTC) is responsible for consumer protection. It takes action against entities engaged in deceptive or fraudulent practices, including those involved in spam and scam calls.
The FTC can bring enforcement actions for violations of regulations such as the Telemarketing Sales Rule (TSR) or other consumer protection laws. Carriers may face fines, penalties, asset seizures, and other legal consequences as a result.
Victims of spam and scam calls facilitated by VoIP carriers may initiate class-action lawsuits seeking damages. These lawsuits can be based on violations of federal or state laws, including the TCPA or consumer protection statutes. Class-action lawsuits can result in significant financial liabilities for carriers and damage their reputation.
Please note that all of these parties can file a lawsuit against you, impose fines and take regulatory action at the same time.
4. Increased Operational Costs

Everything extra that you need to do besides the core business activities is going to add to your operational costs. This will not only eat into your profits but also require you to invest precious time into adhering to all compliance regulations.
Firstly, you have to set up a system or infrastructure in place to be able to monitor and filter all potentially risky calls. Here you have to incur the procurement cost of any additional equipment required and the cost to operate and maintain it.
You will also be required to hire additional people to monitor the calls and act as dedicated compliance officers. This further adds to the increase in operational costs.
Another cost that a lot of people miss out on is the opportunity cost. All the time and business resources that are taken up by compliance requirements could’ve been allocated for other more beneficial activities.
Thus, you’re missing out on opportunities to grow your business and subsequently the profits.
5. Decreased Customer Satisfaction

Increasing compliance requirements due to spam and scam calls can result in decreasing customer satisfaction for VoIP carriers.
To comply with regulations and combat spam and scam calls, VoIP carriers may implement call-blocking or filtering mechanisms. While these measures aim to protect customers, they can also inadvertently block legitimate calls or generate false positives.
This can lead to frustration and inconvenience for customers who may miss important calls or experience disruption in their communication.
Compliance measures such as call authentication protocols or spam detection systems can introduce additional steps in call setup processes. This can cause delays in call initiation or connection, which can negatively impact the user experience.
Customers expect seamless and immediate call connectivity, and any noticeable delays can lead to dissatisfaction and frustration.
Compliance requirements may necessitate additional call authentication procedures. These can include requiring customers to verify their identity or provide additional information before making or receiving calls.
While these measures aim to enhance security, they can add complexity and time-consuming steps for customers. Lengthy or cumbersome authentication processes can result in reduced convenience and decreased satisfaction.
Compliance notifications, while important for transparency, can be perceived as disruptive and annoying. If customers continue to receive unwanted calls, their perception of inadequate protection may lead to a loss of trust and satisfaction.
That was overwhelming, right? As a VoIP carrier, your troubles may increase if you don’t act now and clean your VoIP traffic.
Wondering what measure you can implement to clean up your VoIP traffic? You can try the following 9 ways!
Top 9 Ways VoIP Carriers Can Ensure Spam and Scam Free VoIP Traffic
1. Implement STIR/SHAKEN Framework
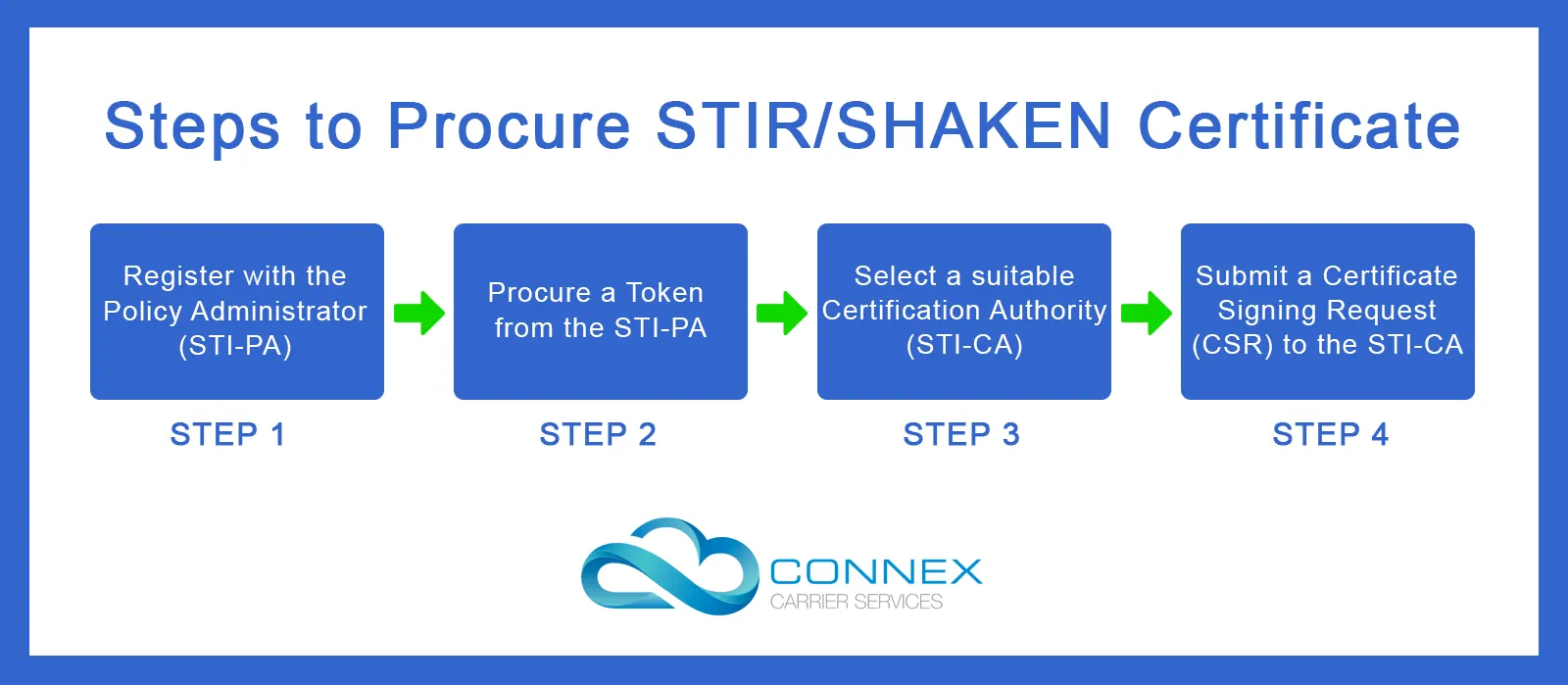
STIR/SHAKEN is a framework designed by the FCC to combat the risk of spam and scam traffic in voice networks, including VoIP systems.
STIR stands for Secure Telephone Identity Revisited, and SHAKEN stands for Signature-based Handling of Asserted information using toKENs.
The STIR/SHAKEN framework verifies the authenticity of caller identification information by digitally signing and verifying calls.
It uses digital certificates to verify that a call's caller ID has not been tampered with and that the call originates from an authorised source.
By implementing STIR/SHAKEN, VoIP carriers can validate and authenticate calls, making it significantly more difficult for scammers and spammers to spoof or manipulate caller ID information.
This helps in identifying and blocking illegal robocalls, reducing the risk of fraudulent activities, and enhancing the overall trust and security of voice communications.
2. Register for the Robocall Mitigation Database

The Robocall Mitigation Database is a centralised system established by the Federal Communications Commission (FCC) in the United States. It is designed to combat spam and scam robocall traffic.
The database serves as a repository for information related to voice service providers' efforts to implement call authentication frameworks.
Voice service providers are required to register in the database and provide information on their implementation progress and their compliance with FCC regulations.
By participating in the Robocall Mitigation Database, voice service providers demonstrate their commitment to combating illegal robocalls.
This helps to establish a trusted ecosystem and reduces the risk of spam and scam robocall traffic by encouraging the widespread adoption of call authentication technology.
The database facilitates the exchange of call authentication information between different voice service providers. This allows each of them to verify the authenticity of caller ID information across networks.
As a result, voice service providers can easily identify and block spoofed or fraudulent calls, making it more difficult for scammers to deceive or defraud consumers.
3. Implement the DNC list and Block all calls to Numbers in it

The DNC (Do Not Call) list is a registry maintained by the Federal Trade Commission (FTC) in the United States. It allows consumers to opt out of receiving telemarketing calls. Consumers can add their phone numbers to the DNC list, indicating their preference not to receive telemarketing calls.
Telemarketers are required by law to check the DNC list and refrain from calling registered numbers for promotional purposes. This reduces the likelihood of receiving unwanted and potentially fraudulent robocalls.
Telemarketers who violate the DNC regulations by making unsolicited calls to registered numbers can face penalties and legal consequences.
The DNC list strengthens the legal framework and enforcement efforts to deter telemarketers from engaging in illegal or deceptive practices.
The existence of the DNC list and its enforcement promotes consumer confidence in the telemarketing industry. With the DNC in place, consumers are more likely to trust legitimate businesses and feel safer from spam and scam robocall threats.
Another benefit of implementing the DNC list is that users are less likely to report legitimate robocalls. This means you spend less time and resources as you won’t be subjected to any investigations for violations.
4. Implement Do Not Originate Framework

The Do Not Originate (DNO) is a call authentication mechanism used to combat spam and scam robocall traffic. It prevents unauthorised parties from using legitimate phone numbers to make spoofed or fraudulent calls.
With DNO, voice service providers can specify a list of phone numbers that are not authorised to originate calls on their network. This list includes numbers that are known to be inactive, unassigned, or restricted for outbound calling.
When a call is initiated, the originating carrier checks the number against the DNO list and blocks any calls originating from those unauthorised numbers.
By implementing DNO, voice service providers can significantly reduce the risk of spam and scam robocall traffic. It helps ensure that calls originating from legitimate phone numbers are authentic and unauthorised use of those numbers is prevented.
This protects consumers from receiving spoofed or fraudulent calls that may attempt to deceive or defraud them.
5. Monitor Your VoIP Traffic

There’s a lot you can unearth just by carefully looking at the VoIP traffic you’re carrying. This process is easier for the more seasoned VoIP carriers who know what spam and scam traffic looks like.
But some are new to the world of VoIP and don’t know what signatures to look for while identifying spam or scam traffic.
Here’s a list of potential identifiers of spam and scam traffic you should look out for:
A. Call Volume and Patterns - Look out for unusually high call volumes or patterns that deviate from normal traffic patterns. Rapid bursts of calls or an unusually high number of calls to specific destinations could be indicative of spam or scam activity.
B. Caller ID Spoofing - Actively look out for calls where the Caller ID information does not match that of the actual originating source. Caller ID spoofing is a common technique used by scammers to hide their true identity and deceive recipients.
C. Call Duration and Frequency - Short call durations or repetitive calls to the same number can be a possible indicator of spam or scam calls. Scammers often engage in brief or frequent calls to maximise their reach and avoid detection.
D. International Call Patterns - Monitor international call traffic, especially to high-risk destinations such as the USA and EU. Unusually high volumes of international calls or frequent calls to countries with a higher risk of fraud can be a strong indicator.
If the traffic of a particular customer checks true for a singular indicator, it may not mean anything substantial. However, if the traffic checks true for multiple monitoring parameters, you will want to investigate it in detail to confirm.
6. Call Content Analysis

Call content analysis helps a carrier leverage advanced technologies to analyse the content of calls in real-time or retrospectively.
Call content analysis examines the audio content of calls, identifying patterns and indicators commonly associated with spam and scam calls. It can recognize keywords, phrases, or voice patterns that are often used in fraudulent activities.
By detecting these patterns, carriers can flag and block suspicious calls, preventing them from reaching customers.
It can also identify robocalls or calls that play pre-recorded messages. It detects the presence of scripted content or repeated patterns, indicating automated or fraudulent calls.
Carriers can use this information to block such calls, reducing the volume of spam and scam calls reaching customers.
Advanced call content analysis can employ voice biometrics to analyse and identify unique characteristics of callers' voices. This helps in distinguishing legitimate callers from potential scammers or spoofed calls.
Voice biometrics can be used to create voiceprints, which are then matched against known fraudulent profiles or used for further analysis and identification of suspicious calls.
This can also identify anomalies in call behaviour, such as unexpected changes in audio patterns, unusual call durations, or sudden shifts in conversation topics.
These anomalies may indicate fraudulent activity or attempts to deceive customers. By flagging and investigating such anomalies, carriers can take appropriate actions to mitigate spam and scam calls.
Please make sure you acquire all necessary permissions required from the customers to sample and analyse the content of their calls.
7. Collaborate with Industry Peers Resources

Collaborating with industry peers and resources can significantly assist a carrier in mitigating the risk of spam and scam calls. Spam and scam calls collectively harm the entire industry. Thus, collaboration for eliminating these is in the interest of all.
Such collaborations allow carriers to share information and insights about spam and scam call trends, techniques, and best practices.
By exchanging knowledge, carriers can stay updated on the latest threats and prevention strategies, enabling them to implement more effective countermeasures.
Sharing anonymized data related to spam and scam calls among industry peers can provide valuable insights into emerging patterns and tactics used by fraudsters.
This collective intelligence helps carriers identify new threats, enhance their fraud detection capabilities, and respond promptly to evolving challenges.
Collaborating with industry peers enables carriers to participate in industry-wide initiatives aimed at establishing standards, guidelines, and frameworks.
Working together, carriers can contribute to the development and adoption of industry standards such as STIR/SHAKEN, which enhance call authentication and verification processes, making it harder for fraudsters to manipulate caller identification.
Collaborative efforts amplify the collective voice of carriers when advocating for favourable yet safe regulatory measures and policies against spam and scam calls.
By joining forces with industry associations, carriers can influence decision-makers, promote stricter enforcement, and shape regulations that address the challenges posed by fraudulent activities.
You could try for memberships in associations such as Internet Telephony Services Providers' Association (ITSPA), Alliance for Telecommunications Industry Solutions (ATIS), The SIP Forum and Communications Fraud Control Association (CFCA).
8. Strategic IP Allocation

Dedicated IP addresses are needed to carry voice media from the caller to the call recipient. When a user reports any call as a scam or spam robocall, the IP address used to carry the media of that call is flagged for everyone to take note of.
Thus, an important evidence-based way to know if any customer is running spam or scam traffic is to see if the IP address they were allocated has been flagged or blacklisted.
This methodology is easy when it comes to identifying bad actors who run large-scale operations. It's standard practice to allocate a dedicated IP address for RTP media to customers who have large-scale VoIP operations.
However, more often than not, an IP address is shared among multiple medium to small scale customers to carry their media. In these instances, it becomes difficult to identify a bad actor and back it up with evidence.
For such scenarios, you can opt for strategic segmentation and allotment of IP addresses to your customers. All you have to do is randomly create cohorts of customers running traffic to high-risk regions.
The next step is to observe if the IP addresses of any groups are blacklisted over a certain period. Chances are you will only have a few cohorts that get their IPs blacklisted.
Once you have segregated clean cohorts from potential bad cohorts, you have to rearrange cohorts at random ensuring proven clean customers are matched up against potential bad actors.
Observe these new cohorts over a period of time and see which ones have their IPs blacklisted. Thus, within a few cycles, you will know which customers of yours are actual bad actors. Once identified, you can take the necessary action to ensure safety.
9. Educate Your Customers and Assist Them To Transition to Cleaner Traffic

Majority of the business owners would never opt for unfair business practices if they can be fairly profitable by following the right business practices. The problem arises when a business owner is not able to generate enough profits using these right practices.
Thus, as VoIP Carriers, if you’re able to educate and assist customers to transition to cleaner traffic, it will benefit both of you.
To start with, your customer won’t have to take unnecessary risks to be profitable. Secondly, you would minimise all the risks as your customer will no longer be tempted to run spam and scam traffic.
Moreover, if you help your customers grow the right way, it is directly going to result in revenue growth for you. Thus, taking care of your customers and pushing them on the right path has a multitude of benefits for both of you.
You may start by explaining to the customers the risks associated with running malicious traffic. Get them to register with the appropriate authorities so they can run any traffic they want within the legal frameworks.
Assist them in growing their traffic in legitimate market segments so they can thrive and won't be tempted to run malicious traffic.
So together, carriers and their customers can make the VoIP industry a safer place!
Conclusion
The risks involved with running malicious VoIP traffic and being an enabler for spam and scam robocalls are tremendous! One wrong move can lead to fines amounting to millions or a complete closure of your business.
In some severe circumstances, you might be charged with criminal offences or face a class action lawsuit. To steer clear of all these possibilities, you need to clean up your VoIP traffic. We’ve highlighted how you can do so in our blog.
I hope this blog was enough of a motivator for you to act right and go clean!
























































































































