Choosing SIP over TCP,TLS and UDP in 2022
VoIP communication changed the way people and businesses communicated. It drastically reduced costs and improved the customer experience.
Cost-effective and quick communication revolutionised customer support and customer relationship management.
With the advent of higher-speed internet, VoIP transitioned from being used on a LAN to being used worldwide. With this came a greater need to choose the right protocol. No longer were networks low latency, low jitter and private
So, how do you choose your protocol communications in VoIP using SIP?
There are multiple options such as UDP, TCP and TLS. Before we compare the three, let’s dive into the basics of everything!
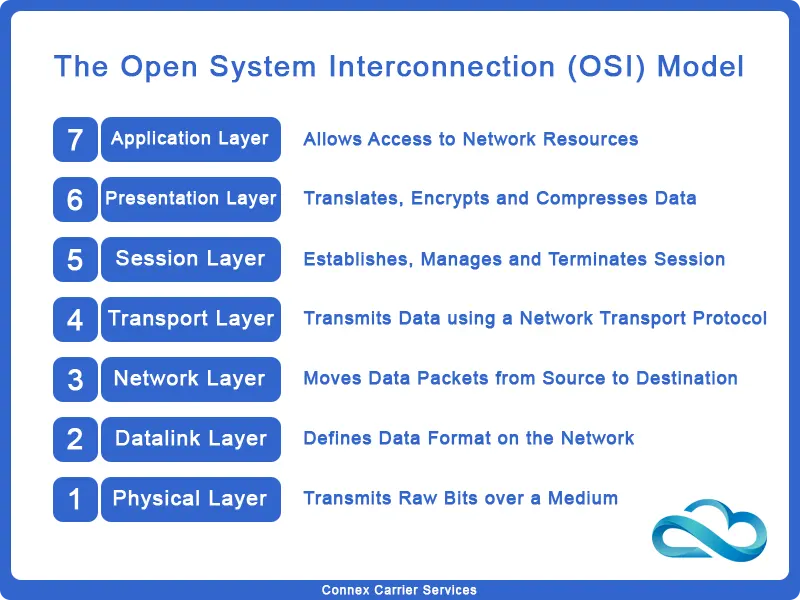
What is Session Initiation Protocol?
The Session Initiation Protocol (SIP) is a signalling protocol that is used to initiate, maintain, modify and terminate a communication session in real-time over the Internet Protocol.
The communication session can contain voice, video, text, or a combination of any or all three media.
So technically, SIP is a universal protocol based on which VoIP functions. SIP itself is based on two other universal protocols viz. HTTPS and SMTP.
To initiate a VoIP call, packets of data are sent across the internet to establish and maintain a direct line of communication. These packets contain the SIP data used to establish the said connection.
There are multiple ways in which these packets can be sent across the internet.
Let us understand how these SIP packets are sent and what considerations need to be made for each protocol.
Network Transport Protocols
When we consider the basics, SIP is an application layer protocol. It was designed to be independent of the underlying network transport protocol.
Thus, SIP can run over different network protocols. A network protocol decides how a SIP packet is transported across the internet.
Every network protocol is different and prioritises a different set of objectives. Knowing these protocols will help you choose the best one for your requirements and keep your communication lines secure.
So let’s dive in and understand the different network transport protocols!
Transmission Control Protocol (TCP)
Transmission Control Protocol, often abbreviated as TCP, is a communication standard that enables applications, programmes and IP-based devices to communicate over the Internet.
TCP was developed by the US Department of Defence to enable accurate transmission of data between defence tech infrastructure.
When two devices or servers communicate using TCP, they establish a formal connection.
When the sender sends a packet to the receiver, the receiver is required to send an acknowledgement packet back to the sender confirming the delivery of packet 1.
If the receiver fails to receive a packet or does not send the acknowledgement packet within time, the sender re-sends that packet to the receiver.
The packets are sent through various routes to their destination and rearranged as per their order at the destination.
TCP is optimised to ensure accurate delivery of data packets and that the data packets are only received by the intended receiver.
This also means that the receiver will receive all the data packets in the sequence the sender had sent them in. For this reason, buffers have to be used, with adds a few ms when receiving the packets.
Transport Layer Security (TLS)
Transport Layer Security, commonly known as TLS, isn’t a completely new protocol itself but an additional layer of security added on top of TCP.
It was developed as an extension of SSL that was in turn developed by Netscape.
In addition to using both public key and symmetric encryption to transport data packets securely, it also has useful features such as authentication and message tamper detection.
TLS ensures no compromise in terms of data integrity and connection security. In doing so it adds additional steps to the already slow TCP protocol.
Implementing TLS adds additional latency to the communication process. However, in applications where security is a top concern, TLS is the ideal protocol to be implemented.
User Datagram Protocol (UDP)
User Datagram Protocol, more commonly termed UDP, is a communication protocol specially used for time-sensitive, low-latency and loss-tolerating data transfers or communications.
In contrast to the TCP protocol, the UDP protocol does not require the sender to establish formal communication with the receiver.
As data transfer/communication is time sensitive, a sender can begin sending data packets directly to the receiver.
Thus, UDP trades the reliability offered by TCP with enhanced speed in terms of communication/data transfer.
These characteristics make UDP the ideal choice for VoIP (Audio Streams), DNS lookup, and audio and video playback.
A major drawback with UDP is that it lacks any error correction capability. This means it cannot assure whether the packets will be received in the intended order. Some packets might also end up lost in the data transmission process.
However, UDP has its upside when it comes to certain applications. The fast speed of UDP makes it an ideal choice for video calls and voice calls.
Let's continue and discuss what protocol is most useful for what application.
Choosing between TCP, UDP and TLS for SIP
Understanding what each network transport protocol does must have given you a good idea about where each one would be the most suitable.
In case you’re still wondering, let us help you with that.
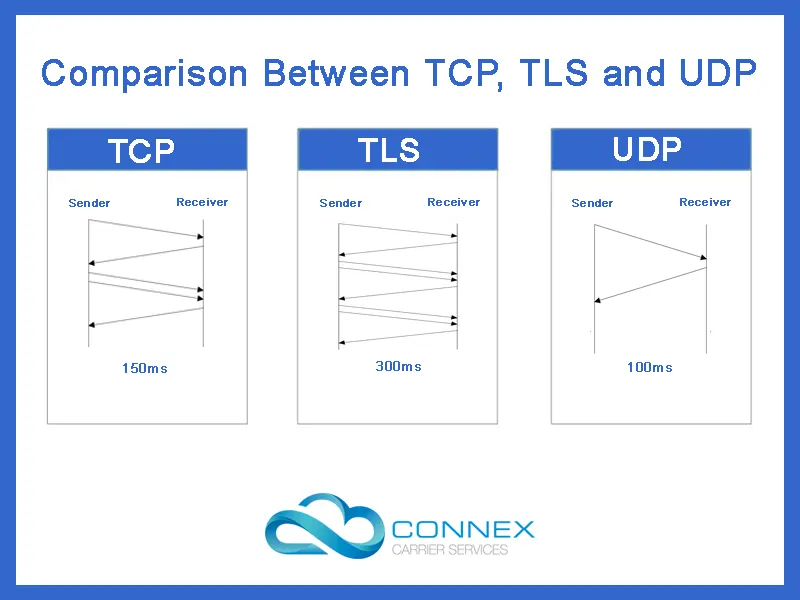
TCP
TCP sits in the middle of the lot with relatively good security, data integrity and reliability. This makes TCP the ideal choice for network transport protocol for communication applications where every call is important. that have relatively low call throughput but require security as well.
For example let us consider a personal communications platform such as WhatsApp, Skype or equivalents. Each user is not going to be generating a high call throughput.
At the same time, data security and privacy are strong concerns for individual users. Thus, TCP fulfils these requirements thoroughly.
TLS
TLS is by far the slowest but the most secure protocol to run SIP over. This makes TLS the ideal choice for VoIP applications that have security as their top priority.
At one time this was only of use for communication between top government administrators or military officials.
But in an information-centric world, privacy is important. Whether this is for PCI or regulatory compliance, or just best practice SIP over TLS is fast becoming in norm to catch up with other communication apps.
Here the call throughput is going to be less. However, security will always be a top concern.
UDP
UDP prioritises high speed which is suitable for time-sensitive communication. Moreover, as it lacks any additional steps for security, it has lower cost overheads among the three network transport protocols.
This makes UDP the ideal choice for communication applications that aren’t a high priority, large in terms of call throughput and cost-sensitive.
For example, you can consider customer support operations for an FMCG firm. While you’re still dealing with customers, such operations do not require much security.
Moreover, as the expected call throughput is going to be high, a lighter and quicker process will always translate into saving for the operator.
To Conclude With
Each network transport protocol prioritises a different set of communication requirements. Choosing the right protocol will always come down to what application you’re looking to implement using SIP.
These three protocols cover all the different sets of requirements any communication application might present. Moreover, as these are standardised universally, it becomes easy to implement and operate your application on top.
So what protocol would you use for your communications?
























































































































